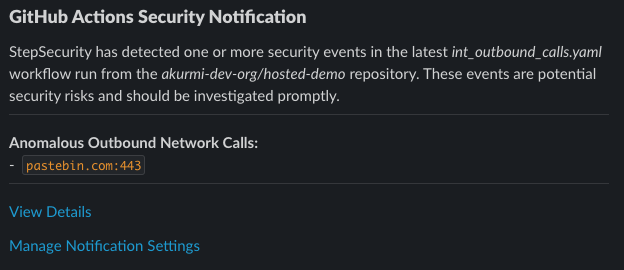
Anomalous Outbound Network Calls
Introduction
In the realm of Continuous Integration/Continuous Deployment (CI/CD), monitoring outbound network calls is crucial for maintaining security. GitHub Actions can sometimes make unexpected outbound network calls, which may indicate potential security risks. This feature enhances the security of your GitHub Actions by training a Machine Learning model of expected network connections across multiple runs of a GitHub Actions job and using this ML model to help you swiftly identify anomalous outbound calls.
How It Works
This feature systematically records all network endpoints accessed by GitHub Actions jobs across multiple runs. Using machine learning, it establishes a model for normal outbound connections. When an outbound call deviates from this established norm, an alert is triggered. This alert is indicative of a possible deviation in your workflow, which could be benign or malicious.
Benefits
This feature allows enterprise and open-source engineers to easily monitor for anomalous events as it functions in Audit mode. If you are using a self-hosted GitHub Actions runner environment such as Actions Runner Controller (ARC) or Virtual Machines (VM), this feature would detect anomalous outbound calls across all of your GitHub Actions workflow runs without any changes in your workflow files.
Understanding the Security Implications
Anomalous outbound calls can indicate a range of security issues, from misconfigurations to sophisticated cyber attacks. On detecting such a call, we recommend immediately reviewing the associated job and conducting a thorough security audit.
For each GitHub Actions workflow job, the platform only sends one notification for a given newly discovered endpoint. It will not notify you in the future as the newly discovered endpoint becomes part of the baseline after the run. Please note that anomaly detection only works in Audit mode. If you are running in Block mode, you would receive a blocked outbound call notification for new endpoints.
Visual Identification on insights Page
We've updated the insights page to help you visually identify such anomalous calls. The insights page now features an icon representing anomalous network calls, highlighted in orange for easy detection.
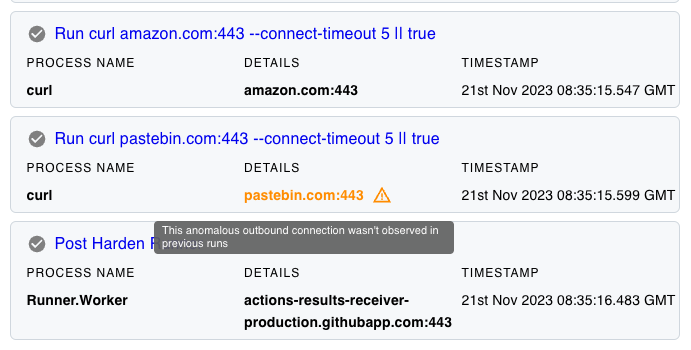
Discover anomalous outbound network calls via notifications
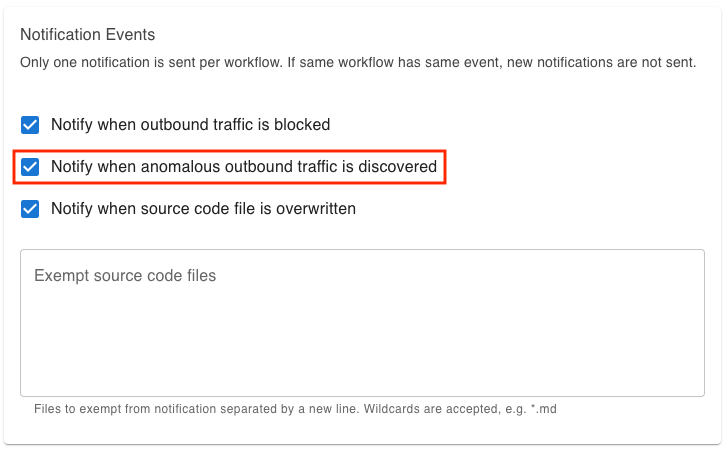
If you have installed the StepSecurity app, you can also enable email and Slack notifications for this alert. You can find details about enabling notifications for your GitHub organization here.
We have added a new option under Notification Event setting to notify your via Slack/email if a new anomalous outbound network call is detected.
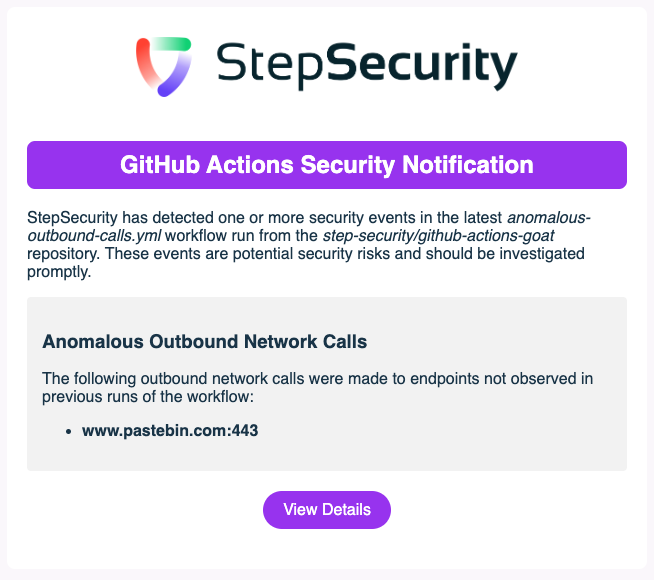
If you have enabled email and/or slack notifications for your GitHub account, the platform would use these channels to notify you anytime it detects an anomalous outbound network call. The notification emails will be sent from StepSecurity <no-reply@notifications.stepsecurity.io>. We have shown sample notifications for anomalous outbound calls below.
Sample email notification:
Sample Slack notification: